
 Working from remote locations, recently has became a standard in many companies. During past few years we have learnt to utilize most of our IT systems, programs and tools remotely such as Office, Outlook, Microsoft Teams, Google Meets, Google Work Space or Google Docs, documentation flow systems or others. Due to significant physical distance to used IT infrastructure, the access to these tools must be properly secured and configured to allow efficient use but third parties, suppliers or other employees have limited access to what you do, in accordance with company’s security policy. Such access is most often implemented in programs through a system of individual accounts in which everyone uses individual logins and passwords.
Working from remote locations, recently has became a standard in many companies. During past few years we have learnt to utilize most of our IT systems, programs and tools remotely such as Office, Outlook, Microsoft Teams, Google Meets, Google Work Space or Google Docs, documentation flow systems or others. Due to significant physical distance to used IT infrastructure, the access to these tools must be properly secured and configured to allow efficient use but third parties, suppliers or other employees have limited access to what you do, in accordance with company’s security policy. Such access is most often implemented in programs through a system of individual accounts in which everyone uses individual logins and passwords.
In large corporate teams with employees working in different locations, this issue is even more important. Although people employed in such teams work in different countries or time zones, many resources must be synchronized with each other and unified access to them improves work, facilitates communication and team management.
Examples of such systems include e-mails, email responders, instant messaging, invoicing, document management systems and many more. In this context, problems appear when the same person needs and access to two or more systems, for example, a contract management tool and document flow management systems. While having many similar situation, hierarchical privileges managements, various systems, remembering several logins and passwords may be confusing for some employees. The desired scenario in such case would be to have on logging gateway that would allow for access to different resources.
Here comes digital identity management!
When an employee logs into the companies resources, he wants to have one digital credentials (i.e. login & password), because in fact he represents the same person in each of these systems. He is also a subject to a specific group of authorizations and rights resulting from the assigned position, duties and other. In such cases Identity and Access Management (IAM) are a perfect choice!
Digital identity is a collection of individual credentials (mostly logins and passwords) that as users, we use in various structures. When we use many systems, we have a lot of credentials. In the long run, this can be troublesome, especially in situations when we forget one of the passwords, because we will need to recover them later. In this case, it is difficult for both users and administrators to manage it.
IAM is a tool that provides effective management of access to information resources. With this solution you can handle the requests of newly hired employees. The identity and access management system also helps in administering users who have parted ways or changed their status with company. With IAM changing or expiring their permissions is much easier.
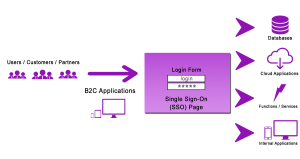
One of the most frequent concepts in the development of IAM is the concept of SSO (Single-Sign-On). It’s a set of systems in which we have one common login point and one common module for managing users and their authorization to all systems. They allow us to manage digital identity in one place. We have one login and password for many systems to which we can log in with the same credentials.
Impact of COVID-19 on Integrated Authorization Management
 In the last two years, IAM systems have been increasingly used due to the need for remote or hybrid work. IAM is of utmost importance in supporting and securing digital resources. Tools like this provide basic authentication and authorization to secure employee data. This goal can be achieved through access management (Multi-Factor Authentication), enabling enterprises to provide end-user authentication to multiple systems.
In the last two years, IAM systems have been increasingly used due to the need for remote or hybrid work. IAM is of utmost importance in supporting and securing digital resources. Tools like this provide basic authentication and authorization to secure employee data. This goal can be achieved through access management (Multi-Factor Authentication), enabling enterprises to provide end-user authentication to multiple systems.

When is Identity and Access Management important?
 Digital identity management actually always happens when we use our unique login. A simple example of using a digital identity is integrating a Google account with the Chrome browser. In the case of corporate solutions, our identity must be better authenticated, so each time we log into the system we have to enter our login and password. Digital identity management occurs when we want to have access to information that is intended only for us, or it requires our interactions.
Digital identity management actually always happens when we use our unique login. A simple example of using a digital identity is integrating a Google account with the Chrome browser. In the case of corporate solutions, our identity must be better authenticated, so each time we log into the system we have to enter our login and password. Digital identity management occurs when we want to have access to information that is intended only for us, or it requires our interactions.
“According to a report by Verizon Data Breach Investigation, more than 70% of employees re-use their passwords at work. The report found that 81% of hacking breaches used stolen or weak passwords.”
The basic principle of creating IAM systems is not to create new security solutions but above all, to use standards and proven security methods instead. Tools that allow us to use standard approaches to ensure the safety and convenience of use in authorization for various connection scenarios of various systems, including:
- Azure B2C
- OAuth2
- Open ID Connect
- Identity Server
- Active Directory
- KeyCloak
- Amazon Cognito
- Google IAM
When mentioning digital identity management, it is necessary to indicate the differences between authorization and authentication. Authorization allows access to confirm whether a given person is allowed to use a resource (e.g. a function or database), and authentication means confirming the identity.

5 benefits of IAM
 Increasing cyber security
Increasing cyber security
Thanks to IAM solutions, companies can implement security policies in all connected systems. Administrators using such tools can easily remove unwanted access permissions when needed, by providing one consistent system of accounts and passwords.
 Lower operating costs in terms of infrastructure management and IT security
Lower operating costs in terms of infrastructure management and IT security
With integrated systems enterprises can benefit from lowering costs in IT infrastructure by minimizing the time needed to solve problems related to the user account.
 More convenient use of systems by users and administrators
More convenient use of systems by users and administrators
By implementing IAM tools, administrators are able to create a unique identity for each user. They don’t have to manage dozens of accounts for different applications or other resources. Users have access to systems regardless of their location, time or device currently used.
 Easier adaptation to the regulations of corporate security policies
Easier adaptation to the regulations of corporate security policies
When ordering or creating software, corporations implement security policies about what can and cannot be done in specific IT systems. If we are dealing with one account logging system, it is much easier to adapt it to security policies.
 Easier password management and recovery
Easier password management and recovery
With IAM solutions, password problems will be minimized. They help administrators implement better password management practices. We are talking about frequent updates of login credentials or stronger authentication.

Identity and Access Management
If enterprises want to keep their employees safe and increase their productivity, they should opt for integrated identity and access management. After logging into the main system, users don’t have to worry about having an appropriate password for other structures. The employee has access to the perfect set of tools to increase his productivity.
“72% of organizations prioritize security over operational efficiency (52%) and tamper prevention (47%) as key factors in the development of the IAM program.”
~According to 2020 IAM Report, Cybersecurity Insiders
Digital identity management is a process that can be implemented in stages. It’s not necessary to integrate all systems at once. Company may decide to implement single systems and add more structures over time.
Inero Software provides knowledge and expertise on how to successfully use cutting edge technologies and data to shape corporate digital products of the future. In recent months we have implemented several cybersecurity solutions based on IAM that allow users to use single sign-on authorization point and securely access corporate systems.
In the blog post section you will find other articles about IT systems and more!




 Increasing
Increasing