What we do in the field of Cyber Security?
We provide expertise in integrated authorization and access management. We build advanced systems for integrated role and user management dedicated for various IT infrastructures. We integrate various authorization flows using well-knows cyber security standards and tools.
![]()
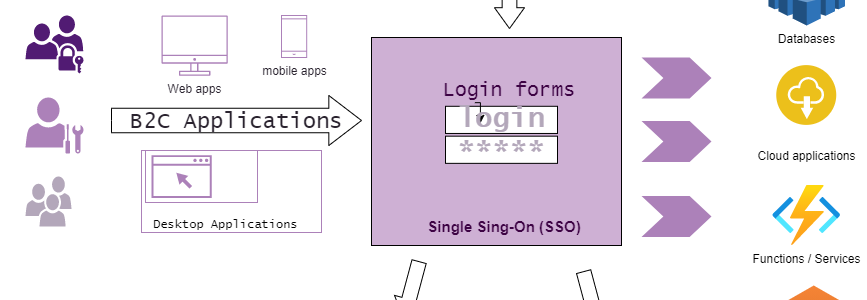
Integrated Authorization Management
![]()
- IAM (Identification & Access Management)
- Single sign-on (SSO) applications
- FIDO (passwordless logging)
- 2FA / MFA (2- and mutli-factor authorization)
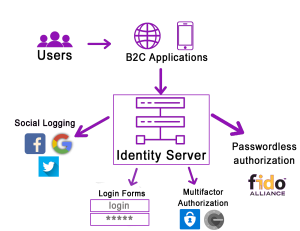
![]() What is IAM?
What is IAM?
Identity and Access Management is tool that provides authentication of application and secure services. Thanks to that you do not need user credentials. This infrastructure helps manage users, roles and access to applications. With IAM difficult account administration won’t be a problem anymore.
![]()
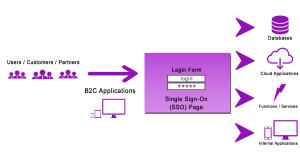
Single Sign-On / Log-in-Just-Once Solutions
![]()
- Azure B2C configuration services
- KeyCloak or Identity Server based identity management
- Integration for all types of IT infrastructures (Saas, cloud, internal, mobile, desktop)
- Roles & User Federation Managmement
- Identity Server / KeyCloak Configuration for SSO views in hybrid software configurations
![]()
Integration With Various Technologies & Security Policies
![]()
- Our solutions are based on OAuth protocol
- Support for VPN access
- CSRF compliant
- Password Policies Roles & User Federation
- Security Event registration
- Support for Time-Based One-Time Password
- User & Roles Administration Console (i.e. Skoruba or KeyCloak)
BLOG

Skoruba for Identity Server – Authorization Module for .NET Applications
.NET Core gives us a lot of possibilities in terms of building business solutions in the logistic, finance or banking sector. Among the most important advantages of this environment are built-in mechanisms of user authentication and authorization, enabling to build requests workflow relying on modules called middleware…