
In our previous post, we demonstrated how to configure Passkeys in Keycloak, replacing traditional passwords with WebAuthn-based authentication. We covered the setup process, key advantages, and potential limitations, including the challenge of user adoption. This blog focuses on configuring Passkeys specifically for mobile devices, ensuring a seamless and secure passwordless experience.
Our first publication about Passkeys in Keycloak, you can find here: An introduction to Passkey with Keycloak
In this post, we’ll dive deeper into optimizing Passkey authentication in Keycloak, looking into a different approach, this time using more than one device.
Using a Passkey stored on a phone
When logging in on a different device, such as a laptop or desktop, users can authenticate using a Passkey stored on their phone. The process works as follows:
- Selecting Passkey Login
Instead of entering a password, users choose the Passkey authentication option. The laptop’s browser generates a request for authentication. Now we have to establish a secure connection between your phone (e.g., iPhone) and your laptop. - Scanning a QR Code
The login interface generates a QR code, which users scan using their phone’s camera. Then the laptop sends a cryptographic challenge to the phone, asking it to sign a request using the stored passkey. The phone communicates securely with the laptop over Bluetooth or other close-range communication protocols (like NFC). - Confirming Identity
Once the phone receives the challenge, it asks the user for biometric authentication (e.g., Face ID or Touch ID). This verifies that the person attempting the login is the authorized user. - Secure Authentication
The laptop checks the response from the phone, verifying the cryptographic signature against the public key registered with the service. If the verification is successful, the user is logged in without having to enter a password.
Step by step: Configuring Passkey with a smartphone
Before we dive into our custom authentication flow, it’s important to check if the Webauthn Register Passwordless required action is enabled in the realm (Authentication -> Required actions tab).
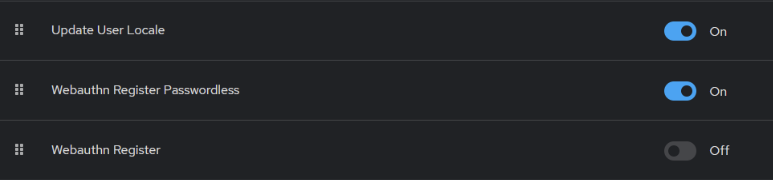
This gives us, for example, the ability to enforce passkey configuration from users after their next successful login. However, it’s important to remember that this is just one of many ways to configure multiple authentication methods.
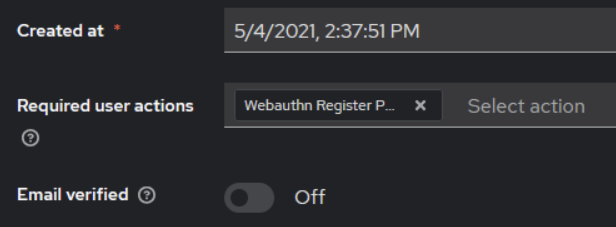
Once we confirm that this option is active, we can proceed with configuring the authentication flow.
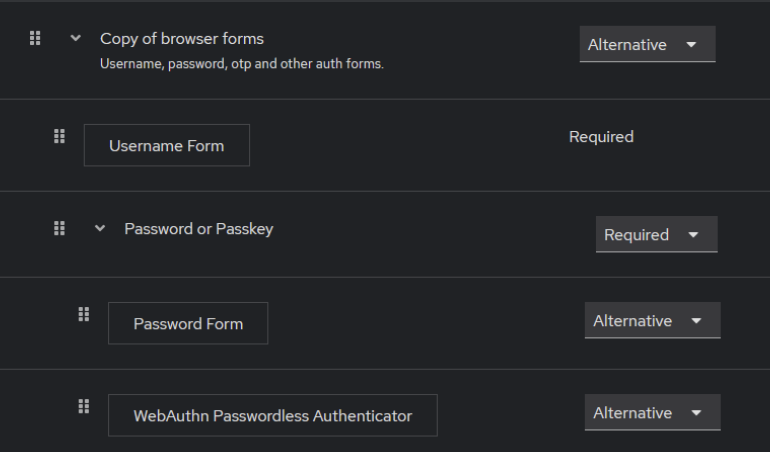
This custom authentication flow for Keycloak is designed to demonstrate how users can choose between password-based authentication and passkey authentication (WebAuthn) during login. Here’s how it works:
- Users are required to provide their username to proceed with authentication.
- This step enforces authentication, but users can choose between password-based login or passkey-based login.
- If the user opts for password authentication, they enter their credentials here.
- If the user prefers passwordless authentication using passkeys, they can authenticate using this method instead.
In this step, users can enter their username or email to proceed with authentication. This is a required step, ensuring that the system identifies the user before offering authentication options.
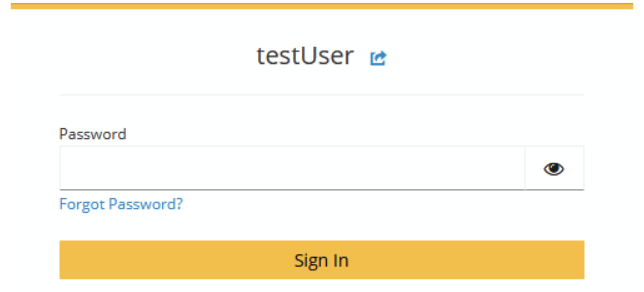
At this stage, we can only use password authentication because we haven’t configured our Passkey (WebAuthn) yet. Once Passkey is set up, users will have the option to choose between password-based and passwordless authentication.
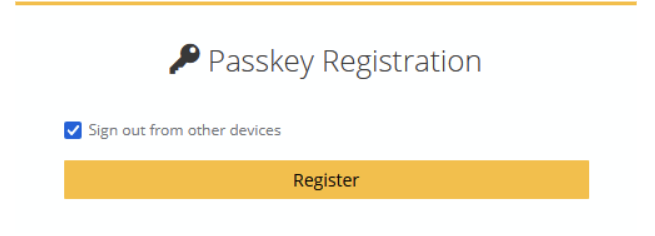
Instead of registering a device PIN as mentioned earlier, we will use authentication via a phone, specifically an iPhone, in this example
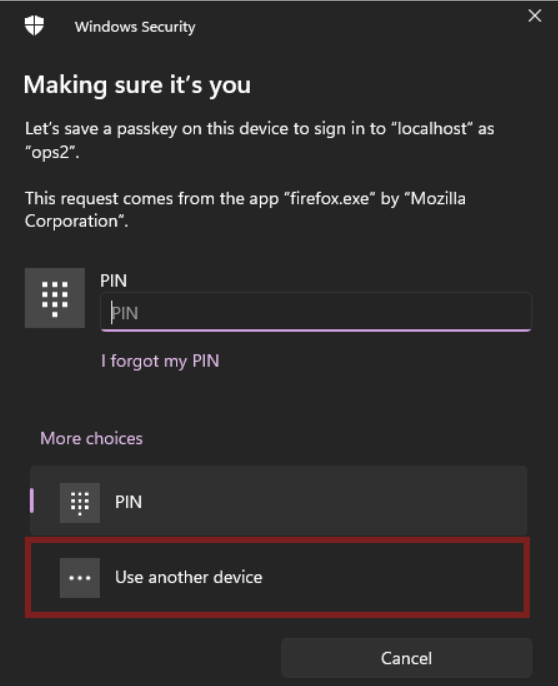
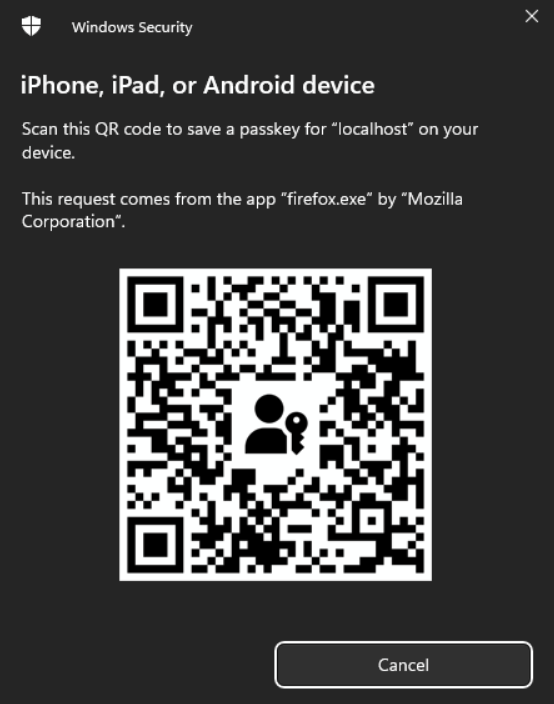
Now, a QR code should appear, allowing us to register a Passkey on our account. Let’s scan it using our phone’s camera and verify the operation, for example, using Face ID.
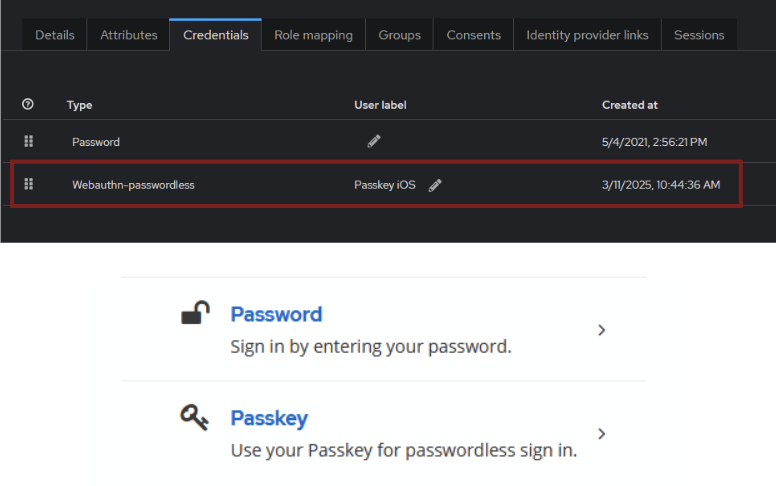
Now, our Passkey should be visible in the Credentials section.
During the next login, we should see the option to choose between password authentication and Passkey authentication.
This setup enhances user convenience by allowing them to pick their preferred authentication method. Passkeys provide a more secure and phishing-resistant login experience, while passwords remain available for users who prefer traditional authentication. With this flexibility, we can ensure both security and ease of access for different user preferences.
It is worth remembering that traditional passwords are a weak link in digital security, often compromised through reuse, phishing, or data breaches. Passkeys offer a modern, passwordless authentication method that enhances security and usability by leveraging cryptographic key pairs managed by platform authenticators. They provide phishing resistance, seamless multi-device access, and compliance with multi-factor authentication (MFA) standards.

