
Keycloak is not just a powerful identity and access management tool; it’s also essential for monitoring performance and enhancing security, particularly when defending against phishing attacks. With its built-in monitoring and alerting mechanisms, administrators can detect suspicious user activities and maintain optimal system performance.

Andrzej Chybicki
CEO Inero Software
Keycloak Performance: Monitoring with Grafana
Monitoring Keycloak’s performance is crucial, especially in large organizations where the system needs to handle thousands of users simultaneously. Interesting tools to use in this regard if for instance aerogear (https://github.com/aerogear/keycloak-metrics-spi). Aeorgear allows for easy trackick of critical metrics in real-time, allowing for system optimization and scaling.
Aerogear provides two key functions: MetricsEventListener and MetricsEndpoint, which enable the forwarding of Keycloak events to Prometheus and integration with visualization tools like Grafana. This allows administrators to monitor important metrics, such as:
Memory usage,
Number of logged-in users (by realm, client, globally, etc.),
Login errors.
Grafana offers a high level of customization, allowing the inclusion of custom parameters (e.g., from CSV files or databases) and setting up alerts. These alerts can be triggered by various factors, such as:
- Exceeding login time limits,
- Logging in from unauthorized locations,
- Unusual numbers of password reset requests.
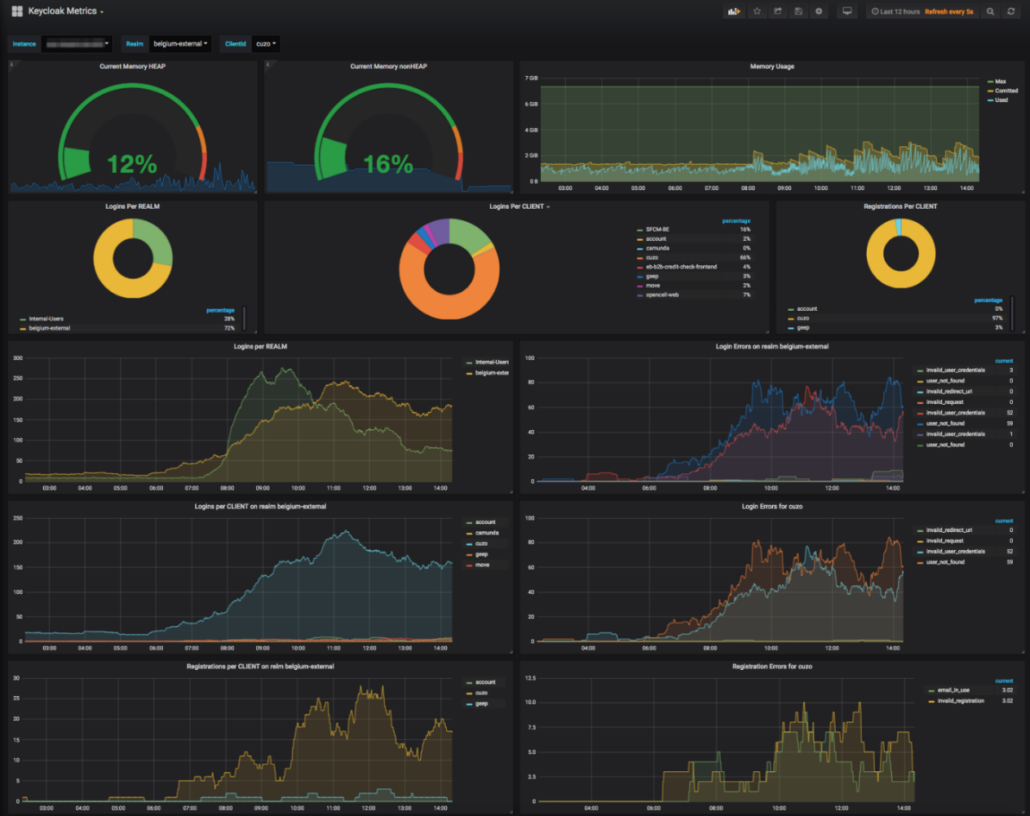
Figure 1. Source: grafana.com/grafana/dashboards/10441-keycloak-metrics-dashboard
Phishing Attack Protection: Adaptive Authentication Mechanisms
In addition to performance monitoring, Keycloak’s advanced built-in security features help protect against phishing attacks by analyzing event patterns. Keycloak events allow administrators to define custom responses to specific user actions, such as password resets following failed login attempts—often an indicator of phishing activity.
An example of a security feature is adaptive authentication, which modifies the user login flow based on previous behavior. For instance, if a user requests a password reset without recent failed login attempts, the system could trigger an additional authentication step, like two-factor authentication (2FA).
Creating and adapting Security Policy
When implementing these features, it’s essential to determine when user actions should raise suspicion. For example, a password reset without failed login attempts might signal phishing, while a reset after multiple failed logins is more routine. A custom security policy could be defined to say: “If a user requests a password reset without failed logins in the last 3 minutes, require 2FA.”
These adaptive authentication mechanisms reduce the burden of MFA (multi-factor authentication) while maintaining high security levels. By configuring Keycloak’s event and alert system, organizations can more effectively detect unusual behavior and respond to potential threats more swiftly.
Keycloak is a versatile tool that supports both performance monitoring and enhanced security. Integration with tools like Grafana allows administrators to keep track of essential system parameters, while advanced event-based mechanisms and adaptive authentication enhance security by protecting against phishing and other threats. Proper configuration of these features can significantly boost security and improve incident response times.

