Introduction
Shipping single sign‑on quickly is tempting. Stakeholders push for a smooth login experience, developers want to move on to core features, and security teams are eager to tick the “MFA enabled” box. The trouble is that identity and access management (IAM) decisions outlive launch days. Once you choose a platform, you inherit its operational model, cost structure and compliance implications for years.
In this blogpost we provide technical leads some few crucial issues when evaluating Keycloak—an open‑source IAM platform that has become a go‑to choice in many Java and cloud‑native environments. Rather than a hands‑on tutorial, you’ll get a decision framework that starts with business realities. We’ll walk through seven questions that determine whether Keycloak fits your context. For each, you’ll see why it matters, how to assess it, the red flags to watch for, and a concrete deliverable to capture the outcome.
By the end, you’ll fill in a short scorecard and see if your organization toward Keycloak, a commercial SaaS IdP (Auth0, Okta, Azure AD B2C, etc.), or a hybrid path. If you want a sanity check, we offer a free 45‑minute Keycloak readiness consultation—no slides, just practical advice.
Where Keycloak Lives in Your Stack
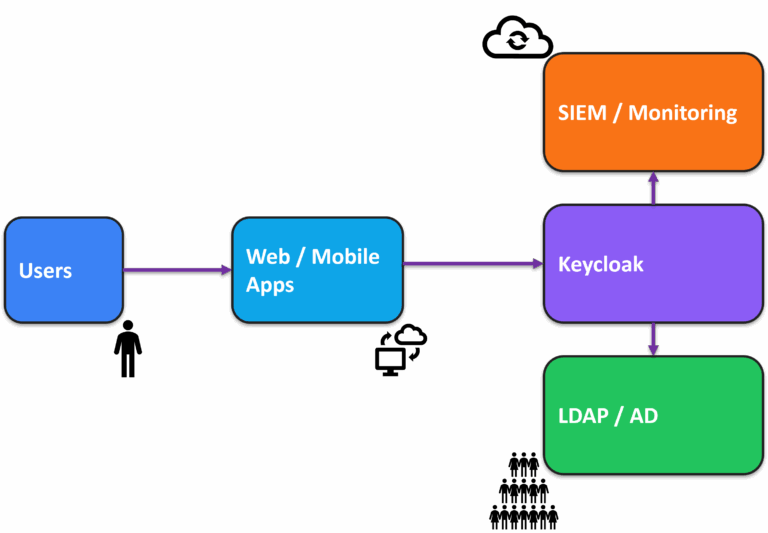
Keycloak usually sits between your user‑facing applications and the identity sources they rely on. Applications delegate authentication and authorization to Keycloak. Keycloak can manage users internally or federate with LDAP/Active Directory. It also exposes logs and metrics that feed your SIEM and monitoring stack. Even if this picture seems obvious to engineers, spelling it out helps align legal, compliance and product stakeholders on who owns what.
Keycloak in a Nutshell (and Two Misconceptions)
Keycloak is an open‑source IAM server supporting OIDC, SAML, MFA, theming and an extension model (SPIs). Originally developed by Red Hat, it now thrives under a large community.
Misconception #1: “Open source = free to run”. The software is free, but production IAM also needs infrastructure, monitoring, upgrades and people. Misconception #2: “It’s just for developers”. In reality, without governance and processes, any IAM platform becomes a liability.
Seven Questions to Frame the Decision
Treat these questions as a workshop agenda, not a checklist. Bring security, operations, product and finance to the same table. The goal is to leave each session with an artifact that informs budgeting, architecture and planning.
1. Compliance & Risk: Do You Need Full Control Over IAM?
Regulatory frameworks such as NIS2 or GDPR—and sector standards like PCI DSS or HIPAA—often demand demonstrable control over identities, audit trails and incident response. If auditors expect you to produce detailed logs or prove exactly who changed what, a black‑box SaaS can create friction
List the controls and evidence you must provide. Do you need to host IAM in a specific region?
How quickly must you produce logs? Are you required to approve every policy change?
If many answers point to tight control, Keycloak’s self‑hosted nature becomes an advantage.
The biggest red flag is deferring compliance: “we’ll pass audits later”. Another is that nobody owns IAM data retention or log policies.
Deliverable: a compliance checklist mapped to IAM features and governance processes.
2. Integration Map: How Many Apps and Protocols Today—and in
Two Years?
Integration effort—not software choice—usually drives project cost and timeline. Keycloak handles OIDC/SAML/LDAP well, but legacy systems and partner constraints can complicate
the picture. Inventory every application that authenticates users. Classify by protocol, business criticality and migration difficulty. Project changes over the next 24 months: new products,
acquisitions, vendor switches.
Red flags: no authoritative app inventory; underestimating testing for each integration.
Deliverable: a prioritized integration backlog with rough sizing.
3. Team & Operations Capacity: Can You Secure and Run It
24/7 (or Outsource)?
IAM outages stop business. Someone must patch, monitor, respond to incidents and plan upgrades. Decide whether your DevOps/SecOps team can own this or you’ll offload parts to a partner.
Assess on‑call capacity, automation maturity, security expertise. Define SLAs, RTO/RPO. Consider managed services for routine ops while retaining architectural control
Red flags: a single overworked DevOps, lack of monitoring/alerting, no upgrade plan.
Deliverable: a RACI matrix for IAM operations and an initial ops budget.
4. Customization Needs: Themes, Extensions and Advanced
Authorization
Keycloak’s extensibility is a major advantage: custom authenticators, advanced policies (ABAC), branded login flows, phishing‑resistant UX. If differentiation or strict UX/security is a
requirement, flexibility matters.
Gauge UX/theming demands, multilingual support, accessibility, device trust, passkeys, fine‑grained authorization.Each adds value to an extensible platform.
Red flags: assuming the default theme is enough; ignoring SPI development complexity.
Deliverable: a customization backlog with effort estimates and ownership.
5. Scalability & High Availability: What Are Your Peak
Loads and DR Needs?
If login fails, revenue stops. HA/DR design impacts infrastructure cost and complexity. You need clarity on peaks, acceptable downtime and recovery objectives.
Estimate peak concurrent logins (launch days, campaigns). Define RTO/RPO. Choose between VM clusters or Kubernetes with an operator. Decide on multi‑region strategies.
Red flags: “we’ll scale later”, skipping DR tests entirely.
Deliverable: an HA/DR architecture option matrix with pros, cons and cost
.
6. Budget & TCO: What Does Three Years Really Cost vs
SaaS?
Keycloak costs = infra + people + consulting. SaaS costs = subscriptions + add‑ons + overage fees.
Only a 3‑year TCO model reveals the truth.
Build a spreadsheet covering infra, backups, monitoring, labor, upgrades. Do the same for SaaS: MAU fees, advanced features, support tiers. Stress‑test both with growth scenarios.
Red flags: ignoring people costs, assuming maintenance is free, overlooking SaaS overage triggers.
Deliverable: a TCO calculator you can keep updating as data changes.
7. Vendor Lock‑In & Roadmap Control: How Much Flexibility
Do You Need?
Open source gives you architectural freedom. SaaS gives you speed but ties you to someone else’s roadmap and pricing. Sometimes that’s fine; sometimes it’s a risk.
Map likely IAM needs for 2–3 years. How critical is it to add custom flows quickly or hold back an upgrade? Could pricing shifts hurt you?
Red flag: ‘we’ll never need to extend’.
Organizations evolve and regulations shift.
Deliverable: a risk matrix—flexibility/control vs speed/convenience—plotting Keycloak, SaaS and Hybrid for your case.
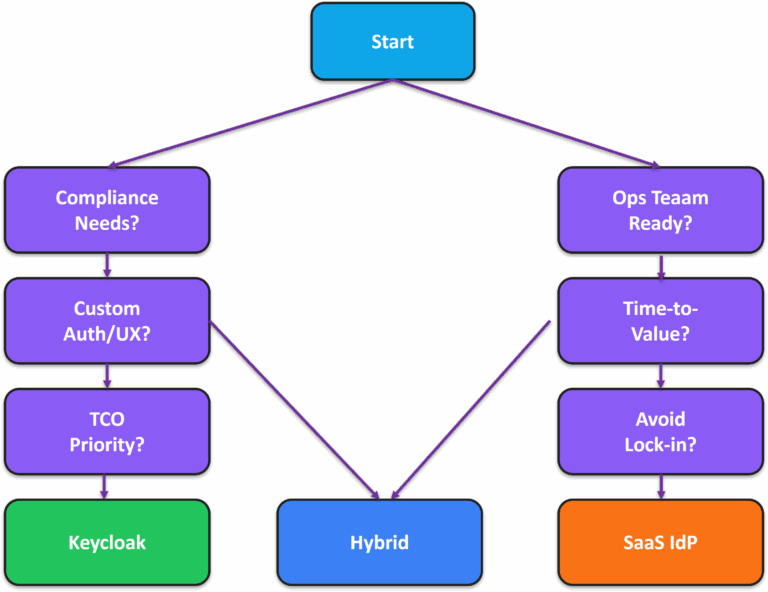
A Visual Decision Flow
If your team prefers a diagram to spark discussion, start with the simplified flow below. It nudges you toward Keycloak, SaaS or Hybrid based on the dominant answers. Use it as an icebreaker, not as a final verdict.
Quantify It: The Scorecard
To make debates objective, translate the seven questions into numbers. Give each one a score from 1 to 5 (5 means a strong push toward Keycloak). Totals near the high end suggest Keycloak or Hybrid; lower totals suggest SaaS. More important than the number is the conversation it forces: why did we give compliance a 5 but ops capacity a 2?
Question | Score (1–5) | Notes | Leaning |
Compliance & Risk: Do You Need Full Control Over IAM? | | | |
Integration Map: How Many Apps and Protocols Today—and in Two Years? | | | |
Team & Operations Capacity: Can You Secure and Run It 24/7 (or Outsource)? | | | |
Customization Needs: Themes, Extensions and Advanced Authorization | | | |
Scalability & High Availability: What Are Your Peak Loads and DR Needs? | | | |
Budget & TCO: What Does Three Years Really Cost vs SaaS? | | | |
Vendor Lock‑In & Roadmap Control: How Much Flexibility Do You Need? | | | |
Total / Recommendation | | | Keycloak / SaaS / Hybrid |
From Decision to Deployment: A Pragmatic Pipeline
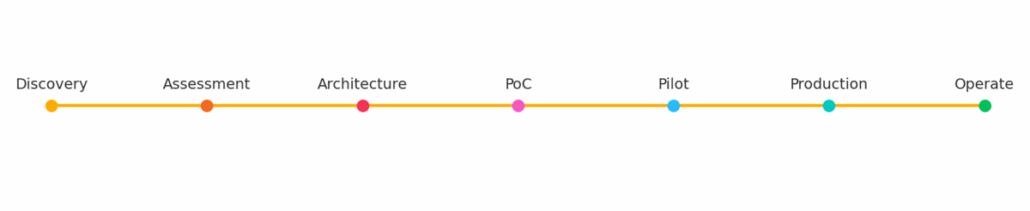
Assuming Keycloak is the direction, you still need a process to avoid chaos. We recommend a pipeline that mirrors proven delivery patterns: Discovery → Assessment → Architecture → PoC → Pilot → Production → Operate. Each phase ends with a clear artifact and go/no‑go gate.
Discovery clarifies drivers, constraints and stakeholders. Without this, technical work drifts. Assessment inventories integrations and compliance needs, and identifies risks and skill gaps.Architecture produces the reference design, HA/DR plan and governance model. PoC attacks the riskiest assumptions first—often a tricky integration or compliance requirement. Pilot rolls out to a subset of apps/users to validate processes, comms and support.
Production rollout happens in phases with rollback strategies (blue/green, canary).
Operate means continuous monitoring, patching, upgrades and cost optimization—often where a partner can help your team breathe.
Next Steps
If your scorecard favors Keycloak, schedule a Discovery & Governance workshop to align stakeholders, draft a high‑level architecture and turn assumptions into a roadmap. If you’re unsure, run a PoC targeting the top two risks. And if SaaS seems better today, design an exit strategy anyway—lock‑in is fine when it’s deliberate, not accidental.
Ready to Validate Your Choice?
Book a free 45‑minute Keycloak Readiness Consultation. We’ll go through the seven questions together, fill out the scorecard and outline concrete next steps—whether that’s an internal PoC, a hybrid approach or a full advisory engagement.
FAQ
Is Keycloak free to use in production?
Yes. The software is open source, but production‑grade IAM still requires infrastructure, operations and security work. Some organizations use managed Keycloak or a consulting partner to offload that burden.
How long does a typical Keycloak deployment take?
A focused PoC can be done in weeks. Larger rollouts with dozens of integrations and strict compliance tend to span several months from assessment to stable production.
Can Keycloak meet NIS2/GDPR requirements?
Technically yes—Keycloak offers detailed logging, fine‑grained policies and MFA, and can be hosted where you need it. Compliance still depends on governance and evidence, not just tool capabilities.