KeyCloak is one of the most widely adopted enterprise identity and access management (IAM) platforms today. At Inero Software, we work with Keycloak on a daily basis — delivering Keycloak deployment, integration, and consulting services for organizations that rely on it as a core security component.
In one of our recent production projects, Keycloak was integrated with a SIEM platform to provide full visibility into authentication and authorization events. Below, we share what this integration looks like in practice — and what really matters when Keycloak operates at enterprise scale.
SIEM as a natural extension of enterprise IAM
In large organizations, IAM is never an isolated system. Authentication and authorization are just one step in a much broader chain of business and security processes. That’s why enterprises rely on SIEM platforms such as Splunk to centralize and correlate events coming from multiple systems.
From our experience with Keycloak-based SSO architectures, IAM events are among the most valuable data points in SIEM pipelines. We previously described the foundations of such setups in our post on
hands-on Keycloak SSO – from setup to integration, where identity becomes a shared service across the organization.
Starting point: no ready-made Keycloak–SIEM integration
Although Keycloak offers extensive APIs and extension points, enterprise deployments often expose gaps that are invisible in smaller setups. In this case, the SIEM platform did not provide a maintained, production-ready connector for ingesting Keycloak events.
This is a pattern we frequently encounter during Keycloak enterprise integrations:
out-of-the-box features cover the IAM core well, but integration with security tooling often requires custom work. Similar limitations — and ways to address them — are discussed in our overview of Keycloak best practices for secure enterprise environments.
Keycloak clustering and consistent event delivery
As is typical for enterprise environments, Keycloak was deployed in a clustered configuration with multiple nodes handling authentication traffic. While events are generated across many instances, the SIEM system must receive a single, consistent security timeline.
Using Keycloak’s cluster-aware APIs, we implemented logic that:
coordinates event delivery across nodes,
ensures that scheduler tasks execute on the appropriate instance only,
avoids duplication or missing data.
This kind of orchestration is rarely mentioned in basic tutorials, but it becomes essential once Keycloak is part of a broader security ecosystem — something we often highlight when discussing enterprise-grade Keycloak operations.
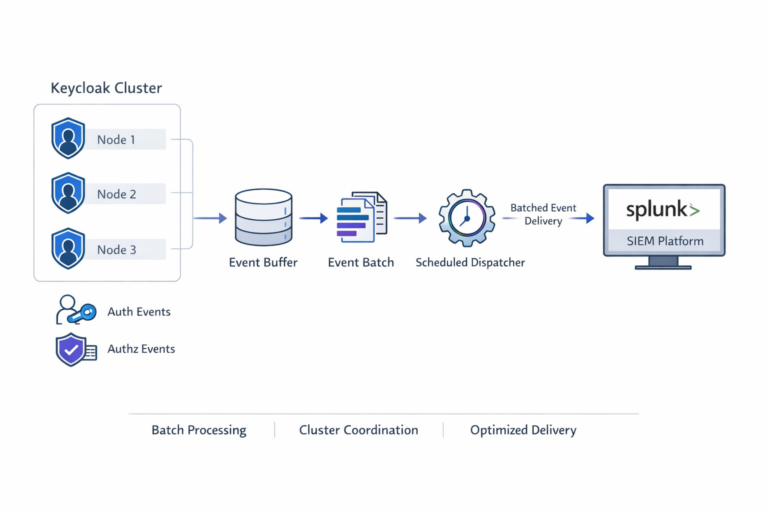
Architectural alternatives for delivering Keycloak events to SIEM
While the core challenge remains the same — high event volume and the need for buffering and batching before delivery — there are two primary architectural approaches to integrating Keycloak with a SIEM system.
Application-level integration inside Keycloak
The first approach is to handle event collection, buffering, and delivery at the application level, directly within the Keycloak runtime. This can be implemented either as custom code or by leveraging existing Java libraries that provide built-in mechanisms for buffering, batching, and reliable event delivery.
Because Keycloak itself is Java-based, this model allows the integration to stay close to the IAM layer and offers fine-grained control over:
which events are collected,
how they are enriched or filtered,
when and in what form they are delivered to the SIEM.
The trade-off is ownership: this approach requires custom implementation, testing, and long-term maintenance, but in return provides maximum flexibility and visibility.
Platform-level integration using Kubernetes agents
The second approach moves the responsibility for event collection and delivery outside of the application, to the platform layer. In Kubernetes-based deployments, SIEM vendors such as Splunk provide dedicated agents that can collect and forward logs and events from applications running in the cluster.
In this model:
the application’s implementation language becomes irrelevant,
buffering, formatting, and delivery logic are handled by the agent,
operational effort is reduced by relying on vendor-supported tooling.
This comes at the cost of reduced control over event semantics and processing, but can significantly simplify integration in standardized Kubernetes environments.
In practice, the decision between these approaches comes down to a balance between control and implementation effort. Application-level integration offers maximum precision and flexibility, while platform-level integration prioritizes speed of delivery and operational simplicity — both valid choices depending on enterprise requirements and constraints.
What we take away from this deployment
Our key takeaway is simple: Keycloak scales extremely well in enterprise environments, but its real value emerges when it is thoughtfully integrated with surrounding security infrastructure.
SIEM integration is not an optional add-on — it is a natural extension of a mature IAM architecture. For organizations operating at scale, this is where Keycloak integration and deployment expertise makes a tangible difference.
At Inero, solutions like this are not experiments or proofs of concept — they are part of how we deliver production-ready IAM platforms for enterprise clients, building on real-world experience rather than documentation alone.

