As organizations expand and incorporate a variety of applications and services, managing user identities across these systems becomes increasingly complex. Keycloak, an open source identity provider, effectively addresses this challenge by offering user federation capabilities. This feature enables the server to connect with existing user stores, facilitating integration and centralized management of user identities. Consequently, organizations can centrally manage user identities without needing to migrate users from their current systems.
Understanding User Federation concept
User federation in Keycloak refers to the ability to connect to external user stores, such as LDAP (Lightweight Directory Access Protocol) servers, Active Directory (AD), or custom databases. This connection allows Keycloak to authenticate and manage users from external sources without migrating users with their credentials. Keycloak acts as an intermediary, handling authentication requests and retrieving user information from the external stores as needed. This makes Keycloak LDAP integration and Active Directory Keycloak integration straightforward and effective.
Key benefits of using User Federation:
- Centralized authentication – users can authenticate across multiple applications using a single set of credentials. It ensures that user data remains consistent across different realms or systems, improving the user experience.This supports centralized identity management.
- Seamless integration – organizations can integrate existing user stores without migrating users to a new system. It helps with onboarding users into new environments by exporting their accounts directly to the target realm. This is particularly beneficial for Keycloak SSO integration and Keycloak custom database integration.
- Improved security – centralized user management enhances security by enabling consistent enforcement of security policies. This ensures adherence to Keycloak security policies.
- Scalability – it supports evolution of organizational infrastructure by enabling smooth transitions and integrations between various identity stores. This helps in Keycloak scalability solutions and managing Keycloak multi-realm setup.
Example Use Case
Consider a multinational corporation that maintains distinct Keycloak realms for different regions, such as Europe and North America. By leveraging the concept of user federation, the company can ensure that user accounts created in the European realm are seamlessly accessible in the North American realm. This allows users to access services across regions without the need to manage multiple sets of credentials, thereby enhancing both user experience and administrative efficiency. This is an example of Keycloak multinational identity management and Keycloak regional user management.
Connecting to external user stores
Keycloak supports various user federation providers, including LDAP and Active Directory. To connect Keycloak to an external user store:
- Log in to the Keycloak admin console and select the appropriate realm.
- Navigate to the User Federation tab and add the relevant provider, such as LDAP or Active Directory.
- Enter the connection details for the external user store, such as the connection URL and bind credentials.
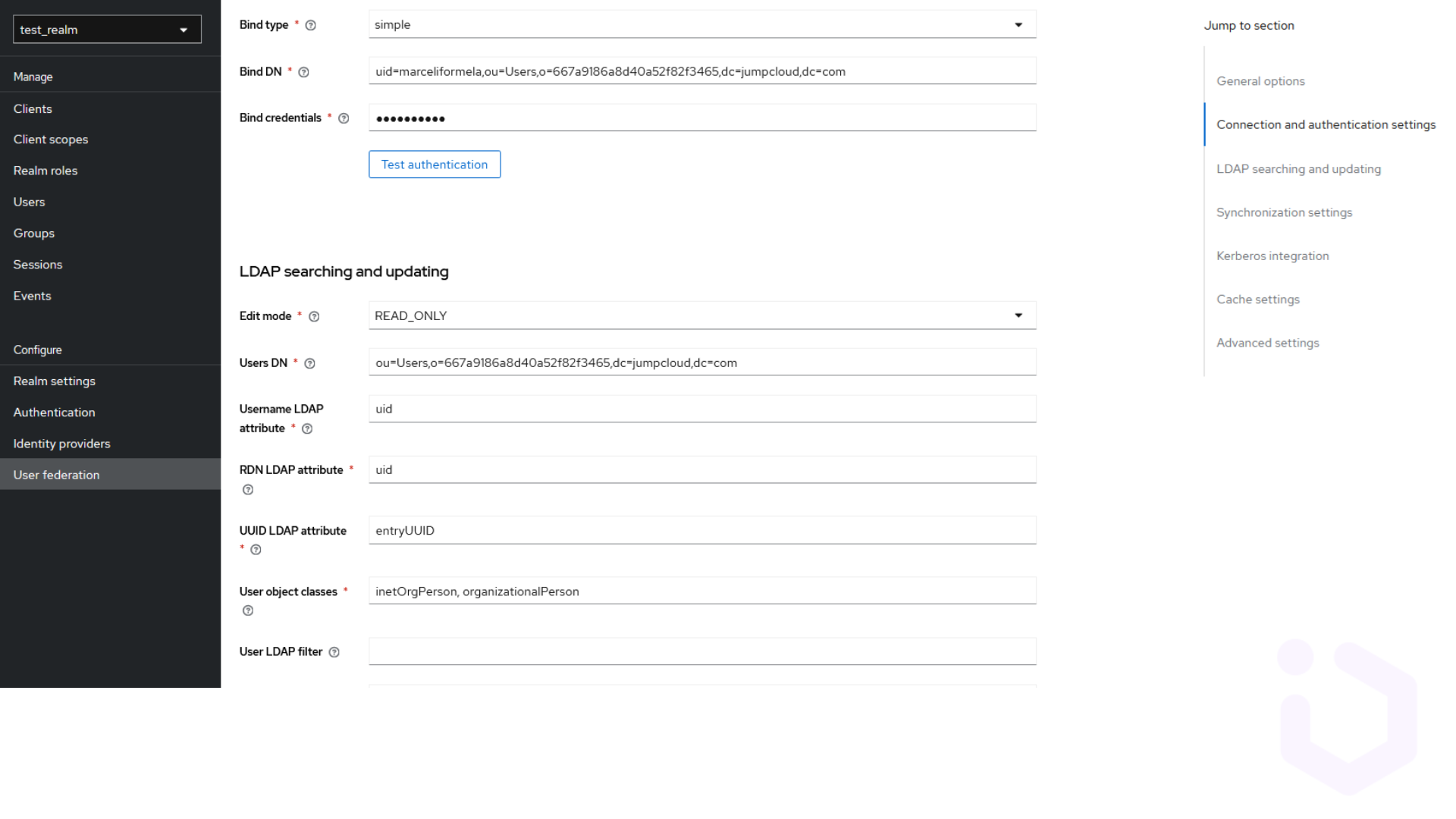
Configuring synchronization settings
By synchronizing with LDAP, Keycloak can leverage existing user credentials, allowing users to authenticate with the same username and password they use across other systems. Sync ensures that user data such as profiles, roles and permissions are consistently maintained between KC and LDAP server.
In import mode, Keycloak periodically synchronizes user data from the LDAP server into its own internal database. This means that user data is copied between the servers. Since data is stored locally, users can be authenticated even if the LDAP server is temporarily unavailable. Also local data access can be faster than querying LDAP for every authentication request. But there is still a potential lag between updates due to periodic synchronization. It is better suited for environments where LDAP server availability might be an issue, where performance is a critical concern, and where there is a need for user data customization within Keycloak. We consider two types of users synchronization:
– Scheduled full sync at regular intervals to ensure all user data is up-to-date. It’s easier to configure and reduces the risk of missing updates or inconsistencies due to overlooked changes. But can also be resource-intensive and time-consuming, especially with a large user base.
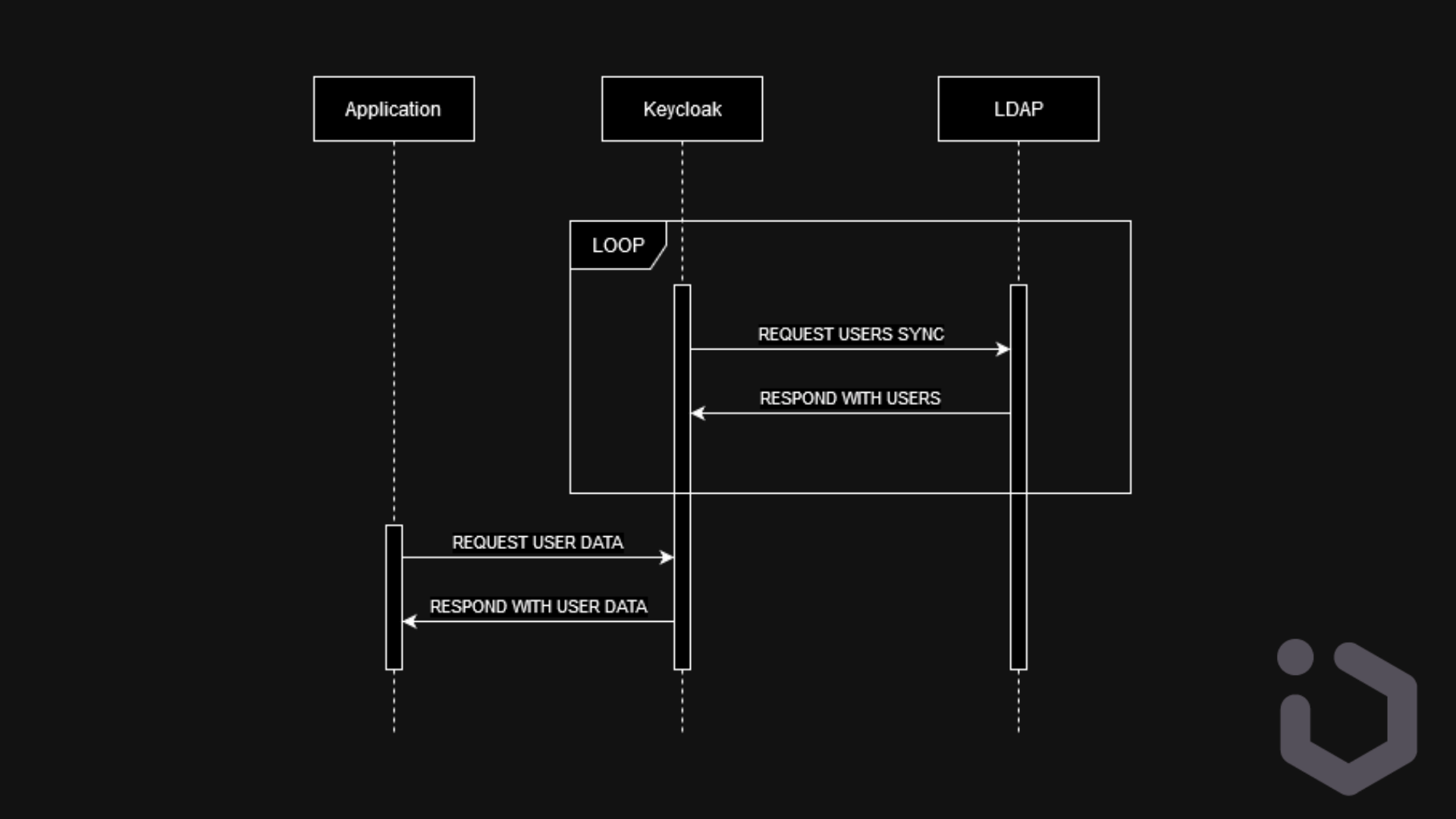
Scheduled full read-only sync with import mode on
– Incremental sync to update only the users whose data has changed since the last sync. With a large number of users, incremental sync is more efficient as it reduces the amount of data being transferred. It is ideal for environments where minimizing resource usage is important.
If import mode is off, Keycloak acts as a proxy to the LDAP server, querying it directly for user information as needed. And no user data is stored locally. This ensures real-time data accuracy as Keycloak always queries the latest data and it also reduces storage requirements as no data is duplicated in Keycloak. In this scenario users may experience latency due to real-time querying. In general, it strongly depends on the availability of the LDAP server for every authentication request. This solution is preferable when data consistency and accuracy are paramount, and the LDAP server is reliable and capable of handling real-time queries without performance degradation.

Managing attribute mappings
There are fields in LDAP that contain user-specific information such as ‘uid’, ‘cn’, ‘sn’, ‘mail’, etc. In Keycloak, these LDAP attributes are mapped to Keycloak-specific user attributes. LDAP attributes can also define user roles. These roles can be synchronized, allowing users to have the same permissions in both LDAP and Keycloak.
Attributes can be used to define conditional logic for authentication and authorization policies. For example, access can be granted based on specific attribute values. They can be later dynamically updated based on user interactions or other events, allowing for flexible and adaptive policy enforcement. In most cases we synchronize them in one direction, typically from LDAP to Keycloak. But in some configurations, attributes can be synchronized bidirectionally, allowing changes in Keycloak to be propagated back and vice versa. This requires careful configuration to prevent conflicts.
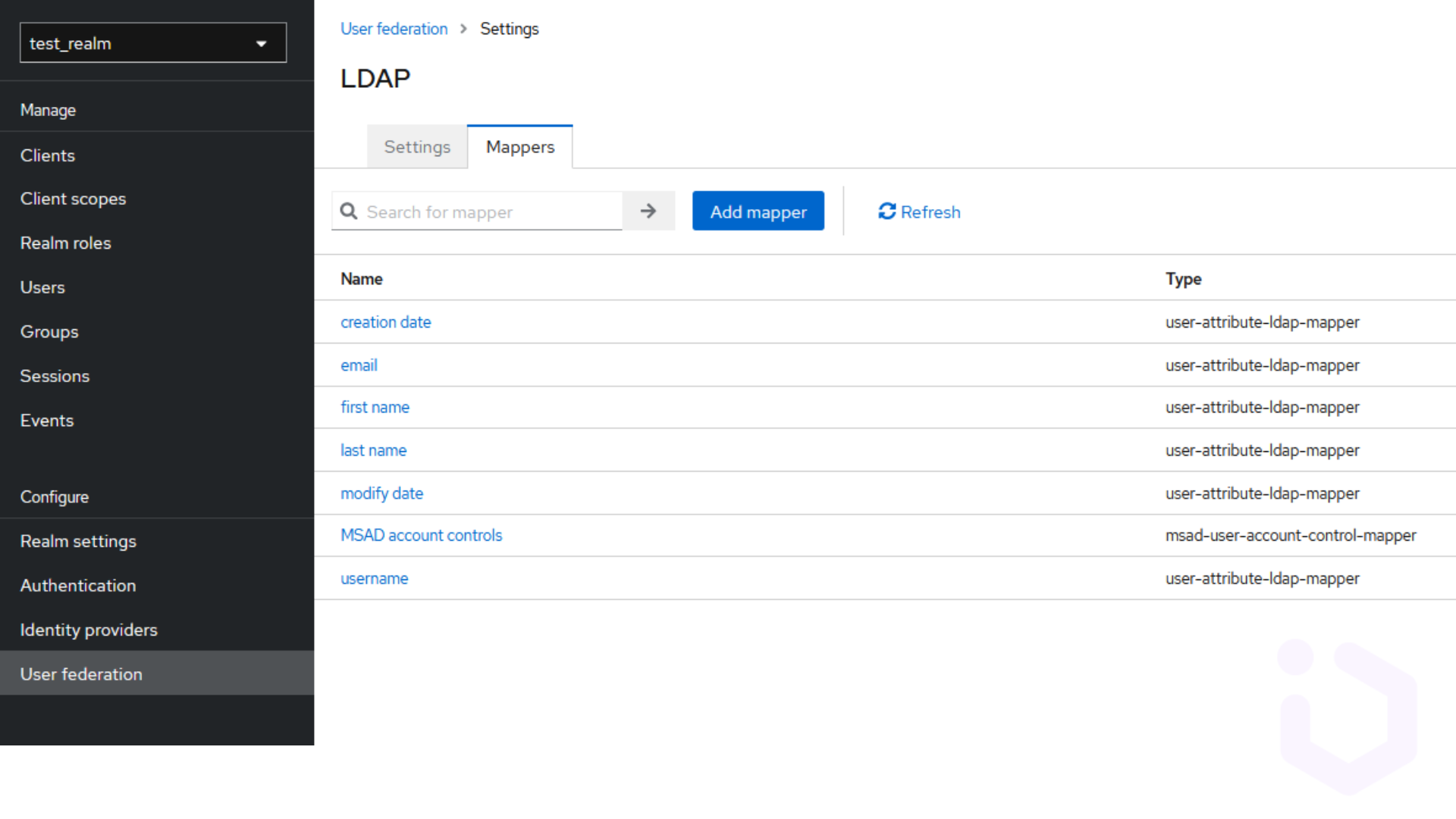
LDAP mappers are used to define how LDAP attributes are mapped to Keycloak attributes. This can be configured via the LDAP provider settings. If default mappers do not meet requirements, custom mapper can be created to handle specific attribute synchronization needs. Attributes can also be transformed during synchronization. For instance, an LDAP attribute storing a full name might be split into firstName and lastName attributes in Keycloak. In some scenarios, attributes from both environments may need to be merged. Keycloak provides mechanisms to handle such merging strategies.
Summary
User federation significantly enhances Keycloak’s user management functionality. It provides organizations with a powerful tool to manage user identities across multiple environments, ensuring data consistency, simplifying user onboarding, and enhancing overall security. By leveraging Keycloak for user federation and account export to federated realms, organizations can streamline identity management and support scalable, secure, and efficient operations.





