
Traditional passwords have long been a weak factor in digital security. They are often reused, easy to compromise, and vulnerable to phishing attacks. Passkeys offer a modern solution by replacing passwords with app-specific cryptographic key pairs managed by platform authenticators. Because passkeys involve multiple authentication touchpoints, they meet multi-factor authentication (MFA) requirements and align with multiple standards.
In this blog post, we’ll show you how to set up Passkeys based on the Keycloak configuration we’ve covered in previous posts (check Securing Java Spring Endpoints with Keycloak or Hands-On Keycloak SSO: From Setup to Integration). While passkeys promise a seamless and secure authentication experience, integrating them into an existing system can come with its own challenges. We’ll guide you through the basic setup process. If you’re looking to modernize your authentication strategy, this is the perfect place to start.
How it works
Passkeys are a passwordless authentication method designed to replace traditional passwords with a more secure and convenient alternative. Unlike passwords, which can be phished, stolen, or forgotten, passkeys eliminate these risks by using cryptographic key pairs stored in a trusted authenticator, such as a smartphone, another device, or a password manager. Instead of manually creating and remembering a password, users enable an authenticator to generate and manage a passkey for them. In general, a passkey consists of two parts:
- A public key, which is stored by the application
- A private key, which remains securely stored in the user’s authenticator
The private key never leaves the device, ensuring that even if the public key is compromised, accounts remain secure.
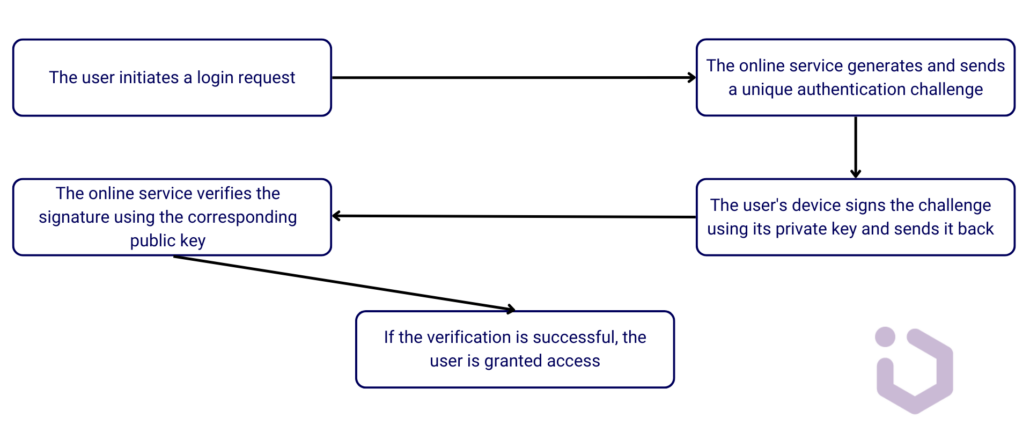
- When logging in, the app sends a challenge to the authenticator.
- The user verifies their identity using biometrics (Face ID, Touch ID), a PIN, or a password.
- The authenticator signs the challenge with the private key and sends it back for verification.
- If the signature is valid, access is granted – without ever needing a password.
Advantages of Passkeys
- Unlike passwords, passkeys can’t be stolen through phishing attacks. They are bound to a specific website or app, meaning they won’t work on fake login pages. Even if a user visits a phishing site, their passkey won’t be prompted and won’t sign them in, preventing credential theft.
- Users don’t have to manage multiple passwords across accounts. Logging in is as simple as using Face ID, Touch ID, or a device PIN.
- Passwords can be guessed, reused, or leaked—passkeys can’t. Even some 2FA methods (like SMS codes) are vulnerable to phishing and SIM-swapping, while passkeys are not. Since passkeys use public-key cryptography, they can’t be stolen or intercepted in a data breach.
- Passkeys are stored in platform authenticators (e.g., Google Password Manager, Windows Hello). They can be automatically synced across devices, ensuring access without manual transfers.
Limitations of Passkeys
- Not all websites and applications support passkeys yet, meaning users may still need to rely on passwords for some services.
- Losing access to a primary device or cloud account could lock users out, requiring recovery options like backup devices.
- Many users are still unfamiliar with passkeys, and the transition away from passwords requires education. Since passkeys don’t require manual entry, users may feel a lack of control over their credentials compared to traditional password management.
Configuring Passkey for the Realm
Keycloak provides flexible authentication options, traditionally relying on passwords and OTP-based multi-factor authentication (MFA). However, with the rise of passwordless security, Keycloak also supports WebAuthn Passwordless (Passkeys). In this setup, we will disable both passwords and OTP authenticators, ensuring that users can only log in using Passkeys.
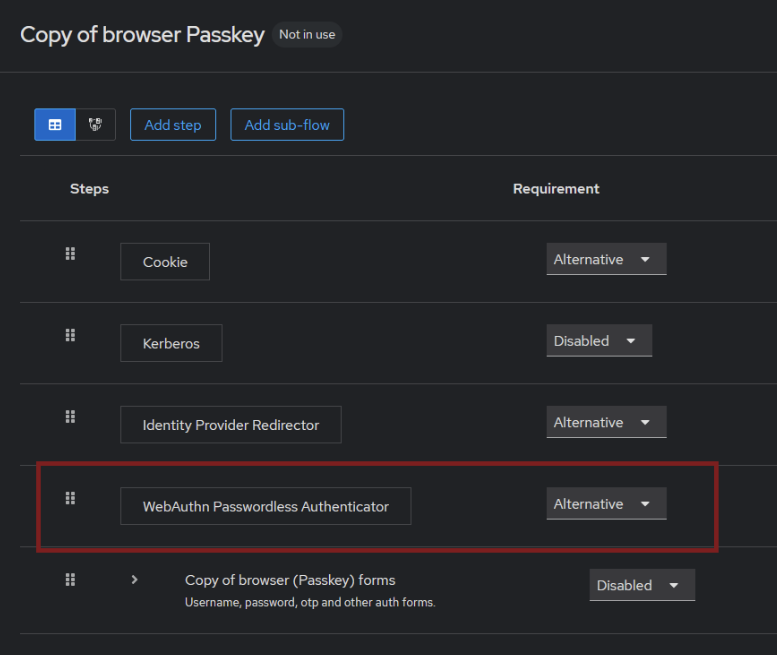
The order of authenticators determines the login workflow in Keycloak. We keep the cookie authenticator to allow users to maintain active sessions. To support external authentication, we enable the Identity Provider Redirect, allowing users to log in via upstream providers like Google, or another Keycloak instance. Next, we configure the actual login form. By default, Keycloak’s browser flow includes username, password, and MFA authentication. We can disable everything in this section and replace it with a single step: adding a WebAuthn Passwordless Authenticator, ensuring that users can only log in using Passkeys. The final flow should look something like this:
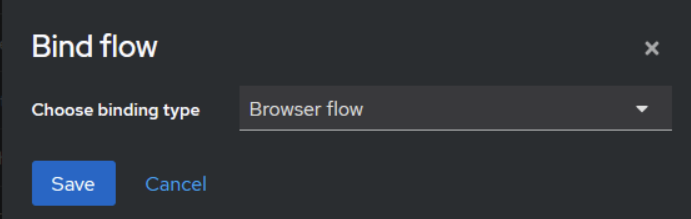
Once the WebAuthn Passwordless Authenticator is set up, the next step is to bind the authenticator to the browser login flow.
Now, all that’s left is to force a password reset for our sample user by setting the required action to WebAuthn Register Passwordless.
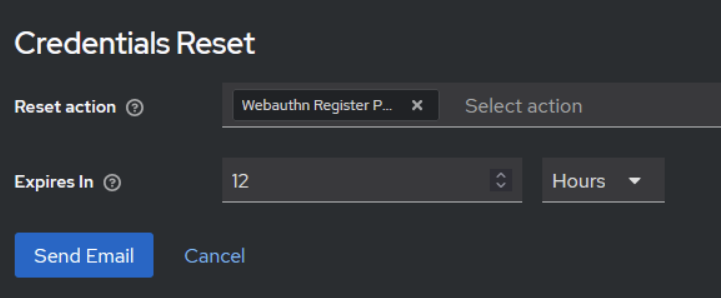
After clicking the link in the received email, Keycloak will display a dialog instructing the user to register their passkey.
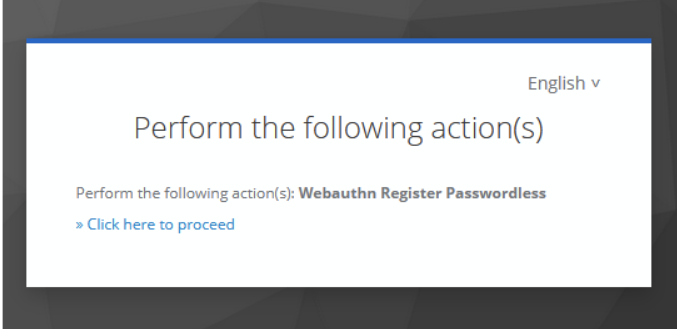
Just click to register the passkey.
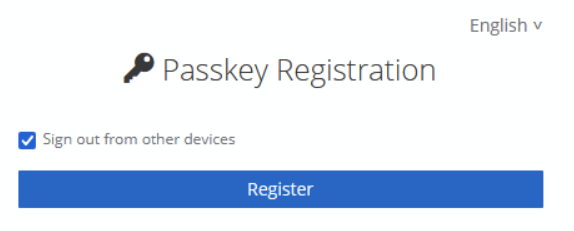
Your device’s platform authenticator will appear showing available options for confirming the user’s identity. Let’s assume we want to use Windows Hello and confirm identity with a PIN code – the same that is used when logging into the Windows account.
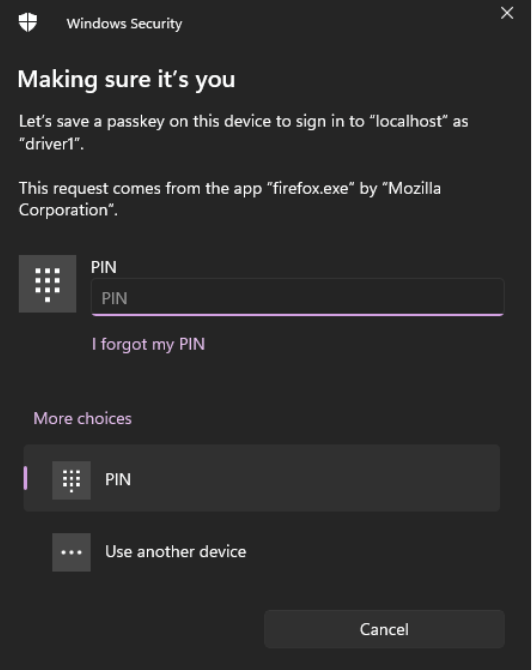
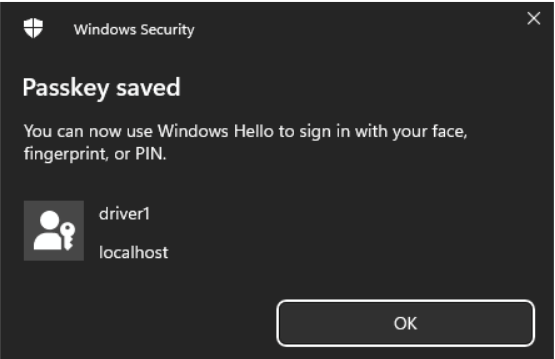
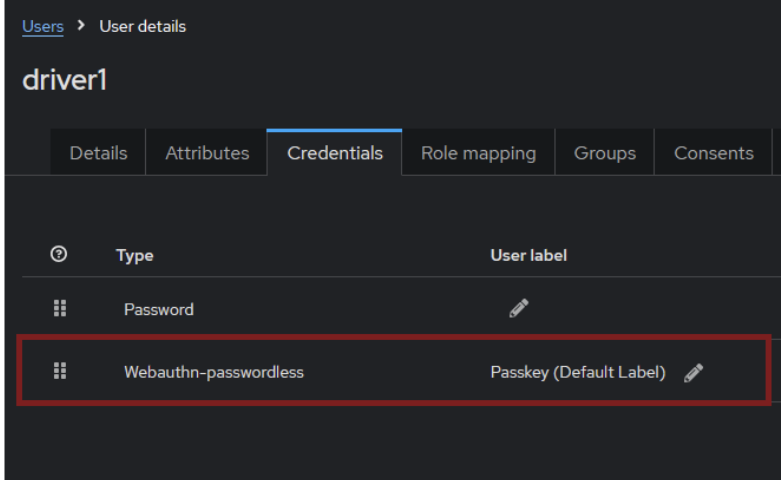
The passkey should now be visible in the credentials section of the specified user.
Now we can go to the realm’s login page and try using our passkey instead of the standard username and password.
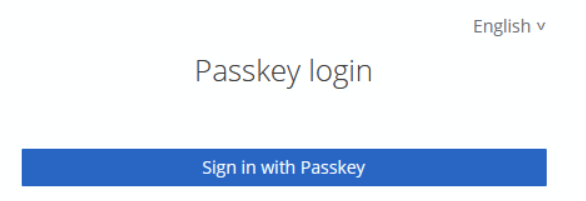
Your platform authenticator should appear again, offering to use the registered passkey.
Passkeys aren’t perfect, but their benefits outweigh their drawbacks for most users. As adoption increases, many of these limitations will be addressed. However, in the short term, users and organizations need to be aware of potential challenges when integrating passkeys into their authentication workflows. Organizations seeking to integrate passkeys into their authentication systems can leverage tools like Keycloak. By integrating passkeys into Keycloak, organizations can provide users with secure, passwordless access to applications while still benefiting from Keycloak’s major features like Single Sign-On (SSO), multi-factor authentication (MFA), and fine-grained access control.

